Search within this section
Select a section below and enter your search term, or to search all click Corp Fin Disclosure Guidance Topics
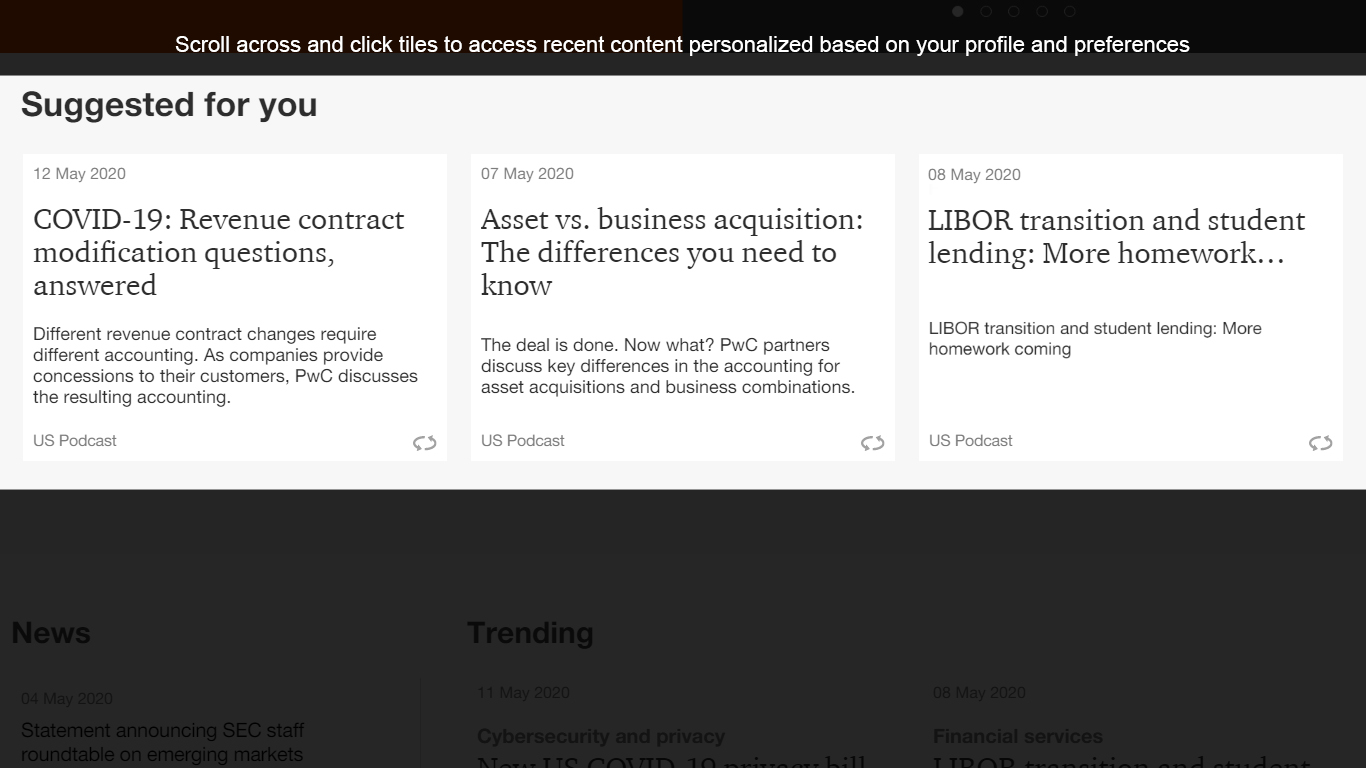
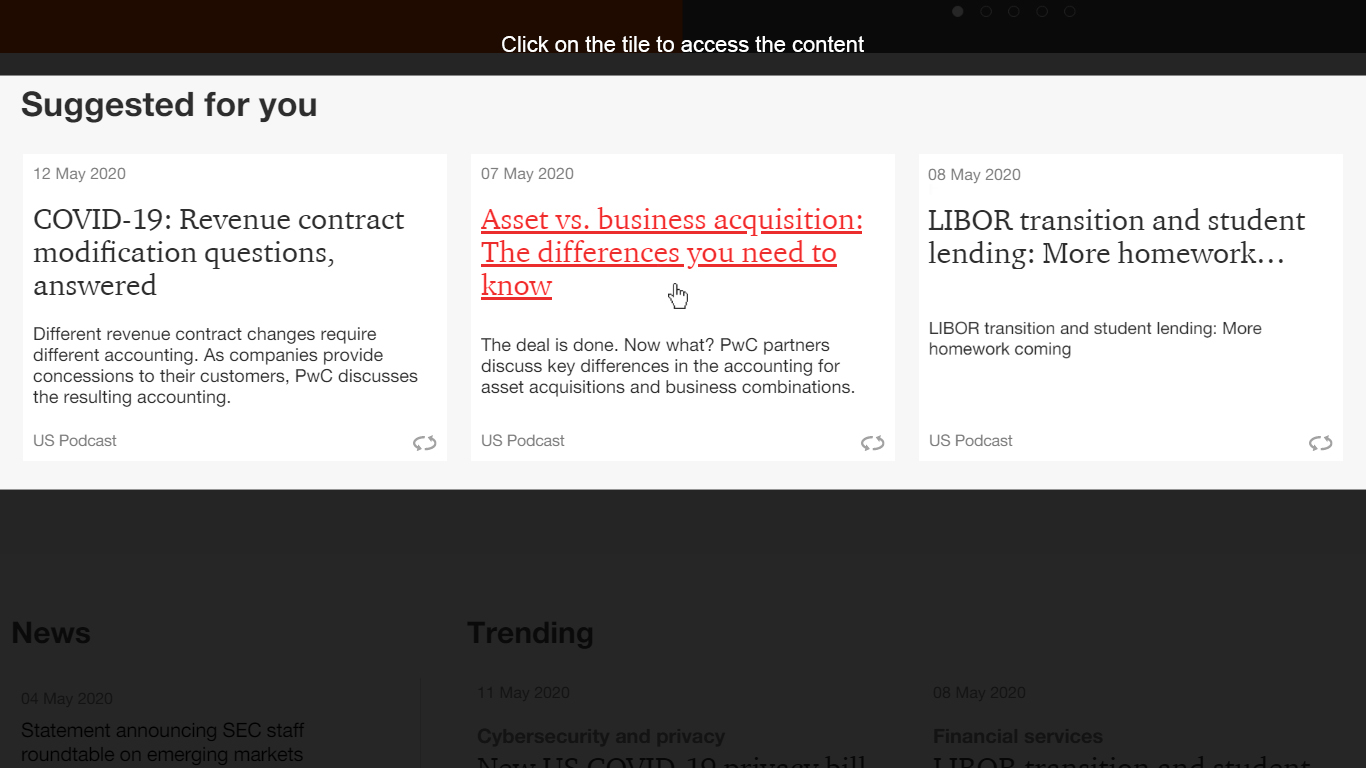
Favorited Content
This is a work of the U.S. Government

Select a section below and enter your search term, or to search all click Corp Fin Disclosure Guidance Topics